Disclaimer: This is part 1 of a two-part post, part 2 here. I used to do quantum research and am now doing a China Studies master's researching the bifurcation issue mentioned in these two posts. If you want to get in touch, you can also find me on LinkedIn.
tl;dr
Quantum technologies could one day be integral to our information infrastructure, with harmful consequences if not deployed responsibly. Quantum computing threatens information security and quantum technologies could enable weapons of mass destruction. Additionally, I believe that risks arising from technological bifurcation and great power competition deserve special attention (see separate post).
While I think that some of the other pathways people in EA are focusing on are likely more important, I make the case for quantum to create awareness and get your thoughts (please leave them in the comments below!). I also want this to be a useful stepping stone for people with a background in quantum or similar to look further into the issues raised in this post.
This post is structured by the ITN framework in the order “Importance” (why could quantum matter?), “Neglectedness” (who works on this?) and “Tractability” (what can be done about it?).
How does it score in these three categories? Quantum technologies score high in impact, are not neglected overall yet some of the most important issues seem to be, and career paths that could make progress on these issues exist, but they often rely on technical expertise in the field. The estimates for impact and tractability should be taken with a large margin of error, due to the early development status of the technology.
Importance
What are quantum technologies and why could they matter?
Quantum technologies could one day become integral to how we sense (quantum sensing), transmit (quantum communication) and compute (quantum computing) information. While mostly limited to research or expensive specialist equipment today, they could become foundational to our information infrastructure decades into the future and have important security implications. Assuming widespread adoption and disruption, quantum technologies will pose many downstream problems if we don’t develop them responsibly.
Sometimes referred to as the “second quantum revolution,” quantum technologies rely on the precise manipulation of information on a very small scale, described by the laws of quantum mechanics. This information could be carried in individual electrons or particles of light, whose quantum mechanical states can be interfered like the acoustic waves in your noise-cancelling headphones. They can also be entangled, i.e. correlated in a spooky non-local way, which is where the parallels to your headphones stop. Conceptually, quantum technologies leverage access to states, and operations on them, which are counterintuitively different from our deterministic interaction with the world–and which can bring practical advantages.
Quantum computing receives the most investments and hype, with people expecting applications in simulating nature, solving optimization problems and, maybe, improving machine learning. Timelines for “useful quantum advantage” vary by who you ask. If you ask experts about breaking currently widely deployed cryptography in the next 15 years, according to a survey by the Global Risk Institute (2023) “a majority of respondents assigns to the existence of cryptographically relevant quantum computer an about even likelihood or better.” If you take somewhat credible company roadmaps, quantum computing could outperform classical computing in some meaningful tasks as early as the late 2020s.
[Useful references: Some relevant applications will be mentioned in subsequent paragraphs, but for a more comprehensive introduction to quantum technologies, I recommend the “professional’s guide” by Quantum Amsterdam, and for a future outlook, the GESDA radar. BCG has published relatively concise overviews for quantum communications and quantum sensing.]
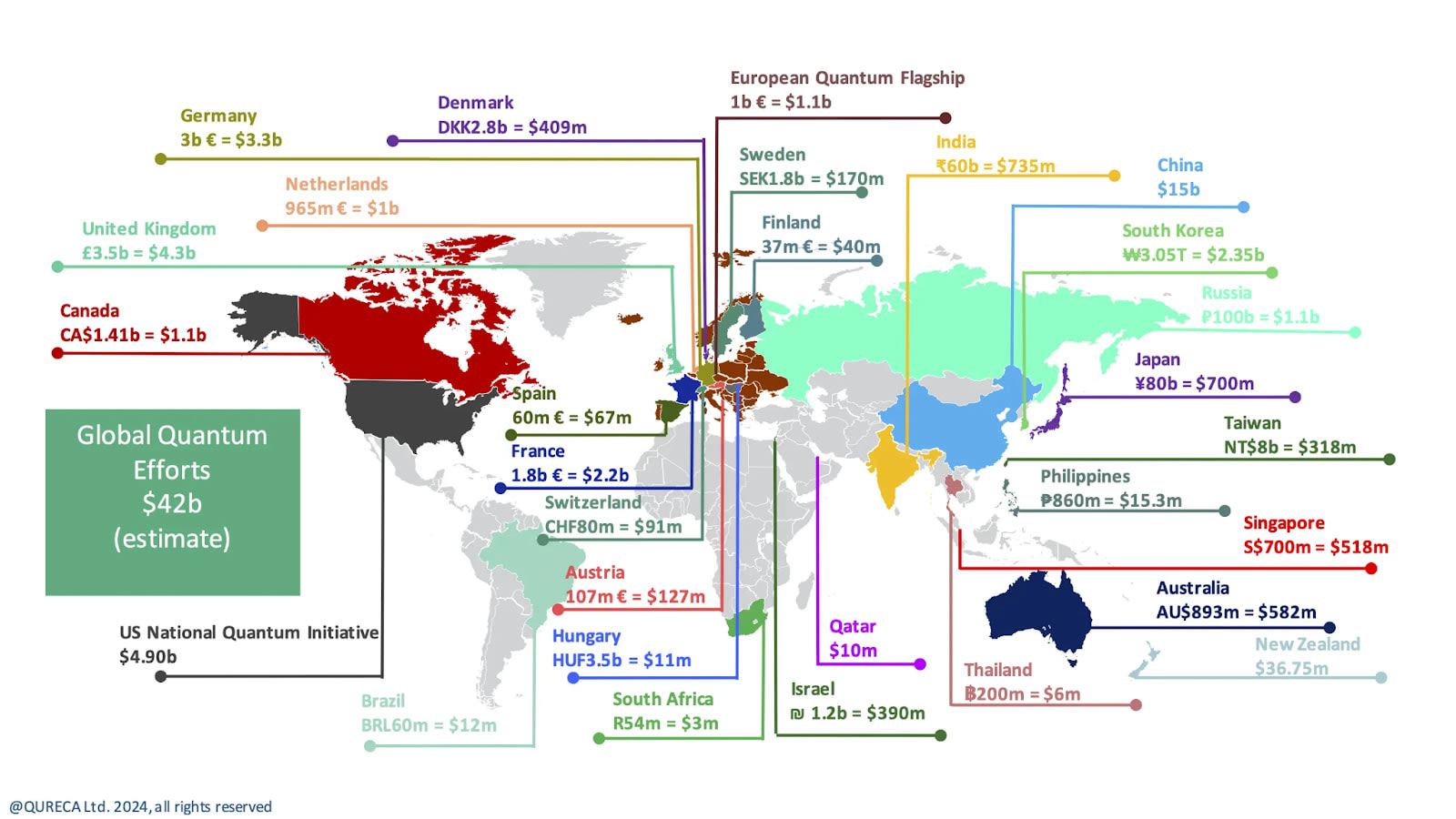
This figure shows global public funding for quantum. Take China’s numbers with a large grain of salt as public funding is not transparent, other estimates put it between USD 4 and 17 billion (the USD 15 billion number largely comes from a RMB 100 billion announcement many years ago for a national quantum lab, reported by media but to my knowledge not in official public announcements).
Most quantum technologies are still at an early R&D stage, except for some sensing and cryptography applications, and much of the worldwide research efforts happen collaboratively in academic settings. However, leading-edge applications and hardware developments increasingly occur in start-ups (low billions of annual VC investments) and large tech companies (IBM, Google, Microsoft, …).
Besides academic and commercial efforts, policymakers are paying more attention (and money – est. USD 42 billion worldwide public funding to date) to quantum technology, aiming to support local innovation. Quantum technologies are prioritised both because of their (potentially) foundational role to the economy and society as well as due to their national security implications. [For an overview of national quantum initiatives, see here]
Personally, given the early stage, I see the long-term outlook as very uncertain: Maybe, in 30+ years we indeed live in a world where millions of quantum sensors, connected by quantum networking infrastructure (“quantum internet”) to data centres full of quantum computers; maybe, quantum technologies will instead remain expensive specialised tools; or maybe, fault-tolerant quantum computing will remain completely out of reach. However, with worldwide efforts and expectations, the parallel pursuit of many different technical avenues and some optimism among the community, it seems hard to completely dismiss a long-term future where quantum technologies will be impactful. If history is any guide, the greatest impacts may not yet be on anyone’s radar.
Because of this potential scale, I would score issues related to quantum technology high on “Importance”–though note that this can result in both large-scale “good” or “bad” outcomes. Here, I mostly focus on the risk of the latter.
What are the most important issues?
Vaguely, I would divide issues related to quantum technologies into questions about their societal impact–with issues like capacity building, sustainability, inclusivity or fair competition–and questions of controlling risks.
With a focus on the latter, here is what I regard as the most important issues:
- Quantum computing’s threat to cryptography: A sufficiently powerful quantum computer can break most protocols securing the transfer of information on today's internet. This could lead to cyber-risks and geo-political destabilisation. Under what’s called “harvest now, decrypt later” encrypted information can be stored today and decrypted once a quantum computer is available. Two methods–one classical (PQC), one quantum (QKD)–exist today to protect against this threat, but both face deployment challenges. More in the appendix.
- Quantum (computing) as an enabler of WMDs: Quantum technologies could advance (bio, chemical or nuclear) artificial design capabilities. Such advances could happen through computational advantages of simulating nature or through experimental advances in engineering nature. This could enable weapons of mass destruction (WMD), although the connection to X-risks such as engineered pandemics seems to me still murky at this point. More in the appendix.
- Great power competition: Race dynamics in obtaining disruptive capabilities arising from quantum technologies could heighten the risk of great power conflict and stand in the way of responsible governance. For example, it has been suggested that advances in quantum sensing could challenge deterrence (e.g. by detecting submarines) or help in countering WMDs (e.g. by identifying dangerous chemical and biological agents).
- Technological bifurcation: I personally believe, that technological bifurcation between China and the “West” is one of the most pressing issues in quantum right now. Bifurcation could exacerbate all issues above, lead to information failures and, if quantum technology will indeed be foundational to future information infrastructure, lead to structural lock-in into competing blocks. A second, related blog-post focusses on this issue.
Note: I did not include quantum machine learning paired with AI X-risks, as to my knowledge, despite much research attention and hype, the prospect of quantum to significantly improve AI capabilities (in a timeline that would be relevant) still faces significant challenges. Of course, this assessment could change over time.
Neglectedness
Are these issues neglected? It depends. On the one hand, a growing number of initiatives have sprung up with a focus on “responsible quantum” and in my personal experience, there is some interest in graduate students working in quantum to take a broader societal view beyond their own research. However, the bullet points mentioned above are often just mentioned in passing or, as in the case of risk from technological bifurcation in quantum technologies, completely neglected. Furthermore, from a cursory search of the forum, it does seem neglected here.
[Useful references: Some organisation that broadly look at the governance or responsible development of quantum technologies: Open Quantum Institute, Quantum Delta NL, Stanford Center for Responsible Quantum Technology, WEF, Quantum Energy Initiative;
Events: Responsible Quantum Technology Conference, RQT Singapore, Responsible Technology Institute]
Tractability
I think it should be very tractable to increase the number of people, especially with technical expertise in quantum, to engage with existing initiatives on responsible quantum (or found new ones).
There are also already many career options to work on the transition to quantum-safe cryptography (be it PQC or QKD). Some of the other risks mentioned are less concrete at this point and it is unclear to me how feasible work on them is today. Still, I believe research on questions such as “how could quantum simulation impact bio-security” or “how to regulate access to quantum computers?” is already needed. I touch on the latter and tractability of working on great power competition/bifurcation in a separate post.
Some more ideas how/where to work on this:
- Prioritisation research; for example on the potential impact of quantum technologies for bio-risks
- Technical research; for example on quantum-safe cryptography or in leading organisations developing quantum technologies*
- Build awareness on the issues mentioned in this post; by publications, science journalism, paper clubs/reading groups, conferences/workshops …
- Work in government/think tanks or in standardisation bodies on issues such as responsible quantum computing or international quantum standards
*An increasing number of “quantum jobs” and consultancy reports highlight the large “quantum talent gap”. However, people considering switching into this field should do careful prior research on the group/company they are joining, as I personally think there are also a growing number of positions that aren’t very meaningful and just go with the hype (see e.g. this rant by someone on reddit about industry positions in quantum computing).
Appendix
Some (hopefully) useful references
Feel free to suggest more in the comments and I will add.
A letter in nature physics calling for responsible quantum: https://www.nature.com/articles/s41567-024-02462-8
Introductions to quantum technology:
For a more comprehensive introduction to quantum computing, I recommend the “professional’s guide” by Quantum Amsterdam, and for a future outlook, the GESDA radar. BCG has published relatively concise overviews for quantum communications and quantum sensing.
Some organisation that broadly look at the governance or responsible development of quantum technologies: Open Quantum Institute, Quantum Delta NL, Stanford Center for Responsible Quantum Technology, WEF, Quantum Energy Initiative
Related events: Responsible Quantum Technology Conference, RQT Singapore, Responsible Technology Institute
Quantum computing threat to cryptography
It is well established (Shor, 1994; and policy-makers are aware, see e.g. this statement by the U.S. White House) that a quantum computer of sufficient scale and quality can break the underlying math problems securing most communication in today’s internet (specifically: Asymmetric / Public-key cryptography, e.g. RSA-2048). Any actor with a sufficiently capable quantum computer could read most information transmitted over distance (health, banking, personal information, chats …) and potentially fake digital certificates (e.g. could pretend to be your bank). Under what’s called “harvest now, decrypt later” encrypted information can be stored today and decrypted once a quantum computer is available.
Assuming cryptography does not fully remedy this “quantum vulnerability” in time, such a capability (through a presumed or real CRQC) could be highly destabilising both in the hands of irresponsible actors or for great power competition (massive information advantage, ability to cause disruption in cyberspace, coercion …). I further discuss this point in my second post on quantum.
How likely is it that this “quantum vulnerability” is mitigated in time? Two main solutions have emerged, Post-Quantum Cryptography (PQC) and Quantum Cryptography (esp. QKD).
- PQC: In the historical context, it is only natural to answer a threat to current protocols with the search for new, better ones. This is the approach taken by (purely “classical”, despite the quantum in the name) Post-Quantum Cryptography (PQC), which replaces existing asymmetric cryptography with one based on new mathematical problems that are not known to be efficiently soluble even by quantum computers. An 8-year effort by NIST (National Institute of Standards and Technology of the United States) has recently released a first set of standardised algorithms. Multiple companies offer implementation / consulting services for transitioning to PQC and the transition.
- Quantum Cryptography, especially Quantum Key Distribution (QKD): An entirely new approach to cryptography, one not based on hard problems but rather on fundamental limitations in the manipulation of information, dictated by the laws of physics. Unlike the conjectured hardness of a mathematical problem used in asymmetric cryptography, Quantum Cryptography is, in theory, secure even against computationally unbounded attackers as long as the laws of physics are correct. Indeed, even intercepting and merely storing the exchanged quantum information is impossible without detection. The best-known Quantum Cryptography is Quantum Key Distribution (QKD). Through the exchange of very precisely prepared states of light, it confidentially shares a password between two parties in different locations. These passwords can then be used with symmetric cryptography such as AES or the so-called one-time pad. Commercialization of the underlying technology began around 20 years ago by companies such as Toshiba or ID Quantique in Switzerland. Today, QKD-secured trial networks have been constructed worldwide, already spanning thousands of kilometres in China.
Why might a transition be challenging despite these solutions?
- Speed: To preserve confidentiality in the future, the transition to quantum-resistant cryptography should have happened yesterday. This is because of store-now-decrypt-later scenarios. According to what is known as Mosca’s theorem, the years prior to the advent of cryptographically relevant quantum computers (CRQCs) that an organisation should transition to quantum-resistant cryptography are greater or equal the transition time plus the time value of the data in question. The transition time refers to the time needed to replace all affected cryptography with a given solution. The planning and execution of this process are incredibly complex, as it affects fundamental algorithmic building blocks in countless devices and pieces of software, potentially third-party and not directly modifiable. If cryptography is implemented on a hardware level or in devices hard to modify after production, imagine IoT or “always on” availability, this time has to account for whole product cycles. Transition time also depends on the technical requirements of the quantum-resistant solution in question: PQC has higher computational and memory requirements and quantum cryptography needs dedicated hardware. Compatibility concerns add further complications. Even simpler cryptography transitions in the past have taken decades to gain widespread adoption. The time value on the other hand refers to the duration that data encrypted today should be secure in the future. For example, national and trade secrets may have time values of decades. Likewise, sensitive consumer data such as in finance or health should be confidential many years into the future, something that is sometimes also regulatory mandated.
- Maturity: Speed stands in an unfortunate trade-off with the technical maturity of quantum resistant solutions. Rushing the rollout of PQC may expose them to implementation attacks, previously unknown attacks on the underlying hardness assumptions, or even suddenly render them insecure—all of which occurred during the NIST standardisation process, validating its necessity while at the same time exposing a dangerous trade-off: Standardise now at higher risk of security breaches and costly patches in the coming years or first continue crypto-analysis, with the risk posed by quantum computers increasing by the day. While Quantum Cryptography is proven secure in theory, it is particularly at risk of implementation errors. Furthermore, being more directly hardware-based in its security and making use of new and rapidly evolving technology brings its own challenges from low transmission rates, quantum attacks that exploit experimental imperfections to high patching costs. Furthermore, some important technological steps such as quantum repeaters or extreme miniaturisation are simply not adequately realised yet. Consequently, quantum cryptography can currently only partially replace existing public key cryptography.
- Economic: Everything outlined above – complex transitions, new hardware and software – will make confidentiality expensive. Economic principles will be just as important as technical principles in dictating who can and cannot enjoy confidential communication. Quantum-resistant cryptography will first be available to those organisations and their clients who have the right combination of expertise, financial resources, and incentive or regulatory pressure.
Quantum (computing) as enabler of WMDs
Simulating physical systems is seen as the most natural and possibly one of the first economically significant applications of quantum computing. Especially in the pharma industry, there are big hopes that this could allow simulating the properties of compounds beyond what’s possible now, massively speeding up and saving costs on experiments.
This connects quantum computing to risks from (democratising) chemical- and bio-engineering as well as nuclear technology. Such concerns are highlighted in the 2023 quantum intelligence report of the Open Quantum Institute / the Geneva Science and Diplomacy Anticipator: “In chemistry, quantum computing could make it easier to discover new drugs to treat neglected diseases, but these methods also could result in the production of more toxic chemicals (chemical weapons, for instance). In material science, the discovery of stronger and lighter materials will help build safer civilian vehicles but also enhance military apparatus. In nuclear physics, modelling forces in the atomic nucleus will lead to more advanced scientific knowledge (i.e., clean and efficient nuclear energy) and the potential for developing more effective strategic weapons.”
These risks are still less clear than the threat to cryptography, where an algorithm is known to break existing cryptography. Indeed, in a previous piece on this forum, Jaime Sevilla concluded that “Very tentatively, I’d guess that the development of QC would not significantly increase bio risk nor it is a specially promising tool for mitigation,” because “artificial biological design is not overly constrained by any single bottleneck”.
Besides quantum simulation as a computational method in artificial design of physical systems, a lot of experimental quantum science is in the first place about artificially designing physical systems at a very small scale to display special properties (quantum materials).
I have no expertise in these artificial design risks and hence struggle to estimate the impact of quantum computing or the design of quantum materials on these risks. However, it does seem that significant research efforts are going into both developing quantum simulation applications and quantum materials. The importance of issues related to WMDs would arguably score higher than the cryptography risk outlined in the previous section.

I have a PHD on computational quantum chemistry (ie, using conventional computers to simulate quantum systems). In my opinion quantum technologies are unlikely to be a worthy cause area. I have not researched everything in depth so I can only give my impressions here from conversations with colleagues in the area.
First, I think the idea of quantum computers having any effect on WMD's in the near future seems dodgy to me. Even if practical quantum computers are built, they are still likely to be incredibly expensive for a long time to come. People seem unsure about how useful quantum algorithms will actually be for material science simulations. We can build approximations to compounds that run fine on classical computers, and even if quantum computers opens up more approximations, you're still going to have to check in with real experiments. You are also operating in an idealised realm: you can model the compounds, yes, but if you want to investigate, say, it's effect on humans, you need to model the human body as well, which is an entirely different beast.
The next point is that even if this does work in the future, why not put the money to investigate it then, rather than now, before it's been proven to work? We will have a ton of advance warning if quantum computers can actually be used for practical purposes, because they will start off really bad and develop over time.
From what I've heard, theres a lot of skepticism about near-term quantum computing anyway, with a common sentiment among my colleagues being that it's overhyped and due for a crash.
I'm also a little put off by lumping in quantum computing with quantum sensing and so on: Only quantum computing would have an actually transformative effect on anything if actually realised, with the others being just a slightly better way of doing things we can already do.
Thanks for sharing this! I agree with some of the things namely
I tried to stress the early state of the technology and large uncertainty, but your comment makes me realize that I should have front-loaded more heavily that nearly all the things I mentioned are long-term concerns.
On the “why now rather than later”, I partly disagree:
Finally, on the “lumping”, it is motivated by the possible future of quantum networking for distributed quantum sensing and interconnecting quantum computers with quantum sensors. Maybe I should have made more explicit in the post that right now, quantum sensors are, as you said, just a slightly better way of doing things we can already do.
I think this is a fascinating area, and the problems you've highlighted seem like important problems. I find it hard to believe it's a cause area EAs should focus on though.
As you explain, the clearest threat is the impact on cryptography, but it doesn't seem likely to me that that problem is neglected. There are huge incentives for governments and companies to solve that problem, and I think they are probably already doing lots of work on it..?
Thanks! I partly agree on the cryptography part, I definitely don’t think that it would be effective to fund efforts towards transitioning to quantum-safe cryptography. Nonetheless, I do believe that working on the quantum-safe transition could be a good career option for someone who already has expertise in the field (feel free to push back on this).
I think in the future, it could be promising to work on capacity building and helping places that lack behind catch up to new cryptography standards. Especially, if real negative consequences start to materialize (which maybe won’t primarily be quantum-enabled hacks but rather compatibility challenges).
Finally, just to clarify, I think that cryptography is the most clear problem, but probably not the most important one from an EA perspective.